What is Cryptography?
In simple layman’s term Cryptography is an art of secret writing. It is necessary when communication in over untrusted network
Major functions of cryptography can be classified in following
- Privacy & confidentiality: To ensure that no one can read or access the message except for the intended receiver
- Authentication: The process of proving one’s identity.
- Integrity: To ensure that the receiver that his received message are not being altered from the original message
- Non-repudiation: A mechanism to cross-check that the sender really sent this message.
- Key exchange: The process by which crypto keys are shared between sender and receiver.
In cryptography “plaintext” is called as unencrypted data. This plaintext is then encrypted into cipher text, which in turn can be decrypted back into plaintext. The encryption and decryption is done depending on the type of cryptography scheme and some form of key.
The usual formula for implementing cryptography is
C = Ek(P)
P = Dk(C)
Here P denotes plaintext, C = cipher text, E = the encryption method, D = the decryption method, and k = the key.
TYPES OF CRYPTOGRAPHIC ALGORITHMS
Commonly used algorithms are:
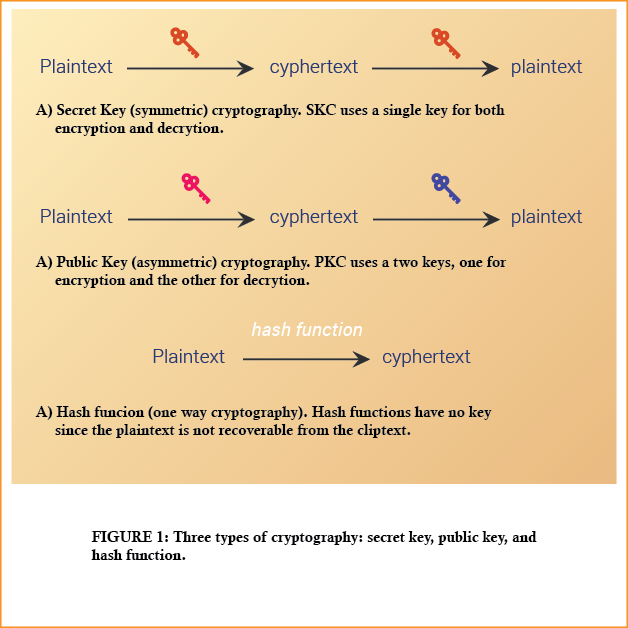
- Secret Key Cryptography (SKC): This algorithm uses a single key for both encryption and decryption; also called symmetric encryption. Primarily it’s been used for privacy and confidentiality of data. As shown in Figure 1A, the sender uses the key to encrypt the plaintext and sends the cipher text to the receiver. The receiver then applies the same key for message decryption and recovers the plaintext. In this form of cryptography, it is obvious that the key must be known to both the sender and the receiver; that, in fact, is the secret. The Main challenge with this approach is the distribution of the key (more on that later in the discussion of public key cryptography).
- Public Key Cryptography (PKC): This algorithm uses one key for encryption and another for decryption; also called asymmetric encryption. Primarily it’s been used for authentication, non-repudiation, and key exchange. Public key cryptography is known as the most significant new development in cryptography. The Generic PKC employs two keys that are mathematically related although knowledge of one key does not allow someone to easily determine the other key. Here the one key is used to encrypt the plaintext and another key is used to decrypt the cipher text. The important thing to keep in mind is that it does not matter which key is applied first, but both the keys are required for the process to work (Figure 1B). Usually in PKC, one of the keys is designated as the public key and may be advertised as widely as the owner wants. Another key is designated as the private key and is never revealed to another party.
- Hash Functions: This algorithm uses a mathematical transformation to irreversibly “encrypt” information, providing a digital fingerprint. Primarily used for message integrity. Hash functions, also called message digests and one-way encryption, and are algorithms that, in essence, use no key (Figure 1C). Usually, a fixed-length hash value is computed based upon the plaintext that makes it impossible for either the contents or length of the plaintext to be recovered. Hash algorithms are mainly used to provide a digital fingerprint of a file’s contents which ensures that the file has not been altered by an intruder or virus. Hash functions are widely & commonly used for password encryption by many operating systems. Hash functions, thus provide a mechanism to ensure the integrity of a file.
TRUST MODELS in Cryptography
Secure use of cryptography requires trust. Even though secret key cryptography can ensure message confidentiality and hash codes can ensure integrity, cannot perform without trust. Hence there are number of trust models used for various cryptographic schemes. This section will explore three of them:
- There is web of trust employed by Pretty Good Privacy (PGP) users, which used their own set of trusted public keys.
- Kerberos, another method of secret key distribution scheme uses a trusted third party.
- Certificates, which usually allow a set of trusted third parties to authenticate each other & its users.
The above trust models differ in complexity, general applicability, scope, and scalability. However it’s hard to define which one is better than the others; everything it depends upon your application.
The PGP’s web of trust is very easy to maintain and is based on the reality of users as people. The model has its own limitation; imagine just how many public keys can a single user reliably store and maintain? There can be chances that you are using the “wrong” computer when you want to send a message and can’t access your key? How easily can a key is revoked if it is compromised?
Kerberos on the other hand has overcomes many of the problems of PGP’s web of trust, for e.g. It is scalable and has a very large scope. However, here only there is a limitation that it also requires that the Kerberos server have a priori knowledge of all client systems prior to any transactions, thus making it unfeasible for client/server in e-commerce world.
Certificates and the collection of CAs will form a PKI. In the early days of the Internet, every host had to maintain a list of every other host; the Domain Name System (DNS) for this purpose introduced the distributed database and DNS is one of the key reasons that the Internet has grown as it has.
Certificates and PKI benefits are associated with electronic commerce, the applications for PKI are much broader and include secure electronic mail, payments and electronic checks, Electronic Data Interchange (EDI), secure transfer of Domain Name System (DNS) and routing information, electronic forms, and digitally signed documents.
Interested to learn more? Watch out this space for our next blog on cryptography testing and how it forms an essential component of BlockChain.
Drop in your comments or queries, at https://www.magicblockchainqa.com/call-us/
Thanks for reading.
Refrences: https://www.garykessler.net/library/crypto.html https://www.tutorialspoint.com/security_testing/index.htm